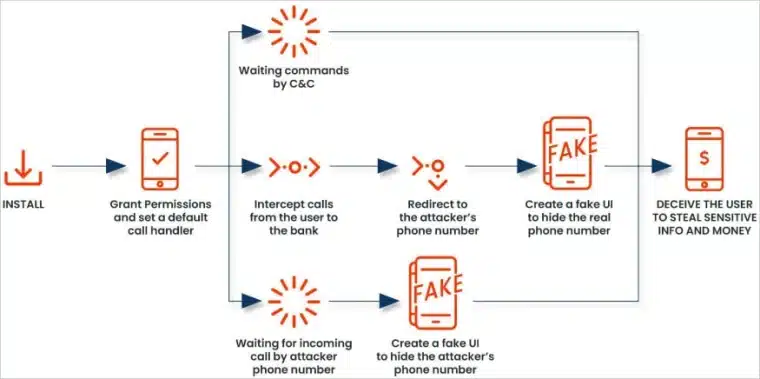
Cybersecurity professionals are warning of a new major attack vector affecting Android devices. Its name is FakeCall and it represents a significant leap in cybercrime techniques as it targets bank customers and their private phone calls to siphon sensitive data from these interactions.
The Trojan was identified by Kaspersky in 2022. Since then, it has undergone multiple transformations to stay off the radar of top cyber security firms.
FakeCall is considered a strategic weapon that endangers the relationship between banks and their customers. Its primary goal is to intercept phone calls to customer support representatives from these institutions and reroute the calls to an attacker-controlled number. Once they have the victim on the line, they extract bank details and personal information to steal their money.
The criminals behind the scheme have created the illusion of legitimacy and have managed to impersonate quite persuasively the protocols and forms used by bank representatives when they interact with customers.
How FakeCall Infiltrates and Manipulates Devices
FakeCall has managed to infect devices by being attached to applications downloaded from websites posing as legitimate mobile app marketplaces. The Trojan also relies on advanced social engineering tactics to gain critical device permissions.
During the installation process, the app will prompt users to set FakeCall as the default call handler. Saying yes to this request gives the software unprecedented access to the device’s communications systems, hardware, and software. The threat of this kind of attack is why you must always be careful about app permissions. If an app (especially a lesser-known one) is asking for suspicious control over your phone (especially as a default call handler), you shouldn’t grant it.
The malware has been designed to detect outgoing phone calls to banks’ customer support numbers. Once these calls are identified, the software activates the re-routing feature and takes over the interaction.
Cyber security researchers found that the permissions granted by users also allow FakeCall to display its own interface on top of the phone’s original one to further deceive users.
Also read: Best Spy Apps for Android : Top 10 October 2024
Zimperium researcher Fernando Ortega highlights the strategic sophistication of recent variants: “The newly discovered variants of this malware are heavily obfuscated but remain consistent with the characteristics of earlier versions.” This suggests a deliberate and calculated approach by FakeCall’s developers to evade detection and expand its malicious capabilities.
Ortega stressed that his security team has identified over 13 variants of FakeCall already. “This suggested a strategic evolution—some malicious functionality had been partially migrated to native code, making detection more challenging.”
FakeCall Keeps Evolving and Gaining More Control of Infected Devices
The latest FakeCall iterations introduce several alarming features that make it even more dangerous than before. These included:
- Accessibility Service Exploitation: By leveraging the Android Accessibility Service, the malware gains extensive control over the user interface. This allows it to monitor dialer activities, automatically grant itself permissions, and even simulate user interactions like clicks and gestures.
- Phone Listener Service: A critical component that establishes a communication channel with the attacker’s command and control (C2) server. This service enables remote commands such as device location tracking, app deletion, audio/video recording, and contact manipulation.
- Bluetooth and Screen Monitoring: While current implementations appear rudimentary, these features suggest potential future expansions of the malware’s surveillance capabilities.
Also read: 4 Tips to Keep Your Personal Data Secure
FakeCall initially targeted Korean-speaking users and banking systems. However, its linguistic support has been expanding progressively. According to ThreatFabric, the malware now supports other languages including English, Japanese, and Chinese (and it likely won’t stop there).
This indicates an ongoing effort to scale the Trojan’s reach to target bank customers globally.
3 Steps to Protect Yourself from This Threat
Experts recommend these three protective measures to avoid having your phone infected with FakeCall:
- Strict App Installation Protocols: Only download applications from official stores like Google Play and meticulously review app permissions before (and after) installation.
- Enable Play Protect: Google’s built-in malware scanning service provides an additional layer of security against malicious applications.
- Scrutinize Permissions: Be extremely cautious about applications that request extensive device access, especially those demanding access to critical communications systems without apparent justification based on the app’s nature and purpose.
Also read: Best Keyloggers for Android 2024: Top 10 Compared
FakeCall represents more than just a singular threat. It reflects the growing sophistication of mobile malware. Its ability to manipulate core device functions, intercept communications, and potentially gain complete remote control of an infected device shows the extent of the cybersecurity challenges that users currently face.
As users continue to rely heavily on their mobile phones to execute financial transactions and communicate with third parties, ill-intended software like FakeCall highlights the critical need for continuous vigilance, user education, and robust security protocols.