It is fascinating to see how extraordinary our daily life has become. Courtesy of Driverless cars, AI robots and state-of-the-art innovation— the future we had been dreaming of is here. This revolution is called the Internet of Things (IoT). In fact, it is estimated that by the end of 2025, there will be 55.75B IoT Devices, creating connectivity of smart appliances, smart grids, self-driving cars, and many more.
IoT is defined as physical systems and information systems colliding with each other. While it brings tremendous advantages into the life of people, it also brings risks in the form of IoT security challenges. In the cyber world, countless people are checking in all the time with an aim to infect the devices by installing video recorders, listening to communications, stealing data, gaining access to code handling and analyzing data at the edge side.
Therefore it’s imperative for organizations to constantly evaluate the risks on the security aspects of IoT devices.
Recent IoT Attacks
Since IoT systems are vulnerable to attacks, they continue to get prone to malicious cyber breaches. Here is a list of significant attacks that shook the world of the Internet of Things:
Xbash Botnet
Malware can harm the computer in various ways and sometimes the effects are not known until it is too late! What’s worse? Your device is getting affected by Botnet (short for Robot+Network). Cybercriminals use special malware to breach the security of several users’ devices and organize all affected systems into a network of bot.
The affected device may operate completely normally with no warning sign but the hacker gets access to create a zombie or bot network which is capable of spreading many different kinds of cybercrimes, such as spreading DDoS or Malware attack.
Mozi
Mozi malware comprises source code from Mirai, Gafgyt and IoT Reaper, which are all part of Malware families that target IoT devices. Mozi is capable of embedding Linux devices with exposed telnet.
Similar to Xbash Botnet, the Mozi malware assembles the affected IoT devices into an IoT botnet which is accessible by the network owner. The owner can easily distribute DDoS attacks, payload execution and exfiltrate data by accessing the network.
Dark Nexus
An IoT botnet that uses DDoS for financial gain, Dark Nexus is a new emerging botnet that leverages compromised PCs, MacBooks and smartphones to stage DDoS attacks through routers, thermal cameras, video recorders, etc.
Recently, approximately 1,372 bots, acting as a reverse proxy are spanning across various locations around the globe such as Russia, China, South Korea, Brazil and Thailand.
Muhstik Botnet
Muhstick Botnet was born in March 2018, and since then it has been affecting the cloud servers by exploiting several web applications. It is a wormlike self-propagating bot that is capable of infecting IoT devices and Linux servers.
Currently, the malware is known to target Oracle WebLogic, Drupal for further distribution of the infected attacks.
The Mirai Botnet a.k.a Dyn Attack
On October 12, 2016, a largely distributed DDoS attack left much of the web inaccessible on the U.S. east coast. How? It was a result of a Mirai Botnet a.k.a Dyn Attack.
It is used by hackers to launch DDoS attacks in IoT devices, upon affecting the device Mirai searches for other malware to completely wipe it out and own that gadget for further exploitation or bidding of data found in the device.
Analyzing Enterprise IoT Security Challenges
IoT has played a major role in enhancing the networking capabilities in organizations. It has helped them to cope with the advanced technological capabilities by developing an effective connection between devices and networks.
Below are some top IoT security challenges that the organizations face –
Insufficient data and updating
Insecure firmware or software is one of the greatest challenges of IoT security. The IoT devices should be updated as to when any vulnerability arises to develop security patches. However, not all enterprises are following the practice. During the update, the backup and data are transferred to the cloud, giving the hackers an opportunity to steal the valuable data of the firm.
Lack of physical hardening
IoT needs to be physically secured autonomously without any mediation. At times, the IoT devices can also physically meddle in remote locations for prolonged intervals. It is a challenge to develop transmitters and sensors to meet with the enterprise IoT security practices checklist. Therefore, it is the user’s duty to secure their devices if the manufacturer has not ensured physical hardening.
Lack of encryptions
In the digital world, hackers are capable of manipulating algorithms that were initially integrated to protect devices that lack storage capabilities and processing. In this case, encryption is considered to be an effective way to prevent breaches. However, even encryption can oftentimes lead to a security alert. To convert it into security support, the firm needs to meet with the enterprise IoT security practices checklist.
Data security and privacy concerns
The various security and privacy concerns related to IoT devices are identification, authentication, and device heterogeneity. In the new digital age, enterprises that lack integration, scalability, ethical communication, surveillance, business models, etc. are the new leads for hackers who interfere in sensitive data and access several private systems in an unauthorized manner.
Lack of proper incident response process
The lack of exercising a proper incident response process leads to loss or exposure of data. In this era, where cybersecurity is top of mind, the cybersecurity incident process is a critical plan for businesses to prevent the leverage of their collected data and information or compromise of login credentials and database exposures.
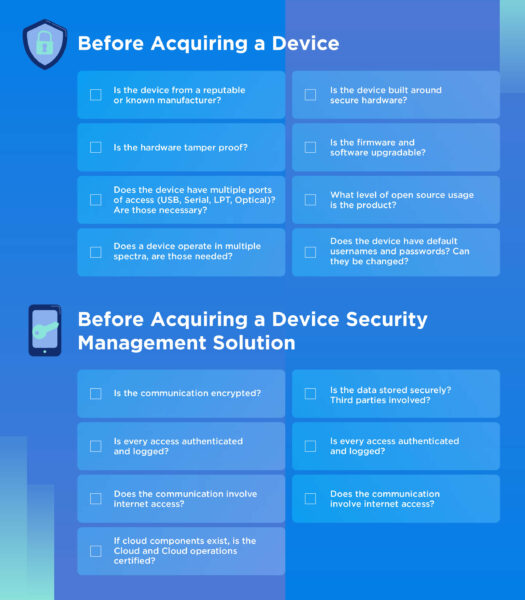
IoT Security Checklist for Connected Products
This checklist covers areas to review in creating a minimal attack surface area, as well as features and actions key to maintaining a secure system in a rapidly evolving field.
Operating Systems
A lot of Linux systems and SOCs have several ports through which hackers can breach security, and this becomes the attack-prone area for hackers. On the other hand, microcontrollers units (MCUs) are known to run their ‘bare metal’ without the support of any operating system. Here, the required communication channel is facilitated by the product developer, thus leaving no ports open for a security breach.
Dependencies
It is essential to incorporate a rigorous system in the Enterprise IoT security practices checklist to keep updating the libraries and external dependencies. Several protocols and encryption are upgraded regularly which means you have to be on top of the game to secure your IoT devices. As dependencies rise, the level of maintenance also rises.
Applications
With multiple applications running the system, the vulnerability and bugs against cyberattacks also increase. Therefore, the applications in the IoT devices should be capable of removing such threats automatically by running an audit.
Communications
To ensure confidentiality, security, integrity and authenticity, proper encryption is a must. The valuable data and information of an enterprise can be compromised if the communication between the cloud and the IoT device is not encrypted.
Cloud
Your server system requires constant monitoring and checks to eliminate IoT security challenges. It is highly advised to subscribe to mailing lists and alerts for your service providers, dependencies, and operating systems. With constant monitoring and minimization of network, application and dependency surface area, the risk can be reduced.
User access and security
Threats are often not easy to identify, even if they are within the company. To combat the same, a strong and positive circle of security and awareness within the team is a must. Further, simple yet effective practices like strong passwords, two-factor authentication and encryption can help avoid user damage.
Overview of IoT Security Practices Checklist
Enterprises should be proactively aware of possible risks introduced by IoT devices, understand the scale of the landscape they are forced to secure, educate the team on IoT security challenges; and strike a balance between maintaining device security and keeping employee productivity in mind to meet business objections. This enterprise IoT security practices checklist provides important considerations for securing IoT devices in any size organization.
Actions for IoT Security
All systems require maintenance to stay ahead of evolving security risks. Here are few actions you need to take to bolster your IoT security
Vulnerability assessment and penetration testing
Enterprises can stay at the top of their game by staying ahead of advanced hacking techniques by regularly testing their systems with IoT Security Testing tools, thereby fixing vulnerabilities and bugs as and when they develop.
Firmware application reviews
The experts are required to sanitize the application bugs during the development of firmware to prevent applications flaws and bugs at a customer level.
Security updates and patching mechanisms
Security updates and protocols keep updating from time to time. To secure enterprise IoT, rapid firmware deployment should be made accessible to all devices.