Cybercrimes have been on the rise over the last few years as the world goes increasingly digital. While many cybercriminals target individuals who they perceive as gullible, a new kind of malware has been targeting organizations in a massive ‘copyright infringement’ phishing scam. In this article, we break down the scam, dubbed the Rhadamanthys infostealer malware, and how one can keep safe from these attacks.
For context, since July, Check Point Research has been tracking a phishing campaign where bad actors are sending emails to organizations pretending to be “legal representatives” for companies mostly in the media, entertainment, and technology sectors. The emails, generally sent using Gmail accounts, falsely claim a copyright violation on the company’s social media pages and request the removal of some videos and images.
Even Check Point was impersonated in one such case where scammers claimed to be legal representatives of the company. In their communication, they said that the recipient was “illegally using” their images and videos to advertise products on their Facebook page.
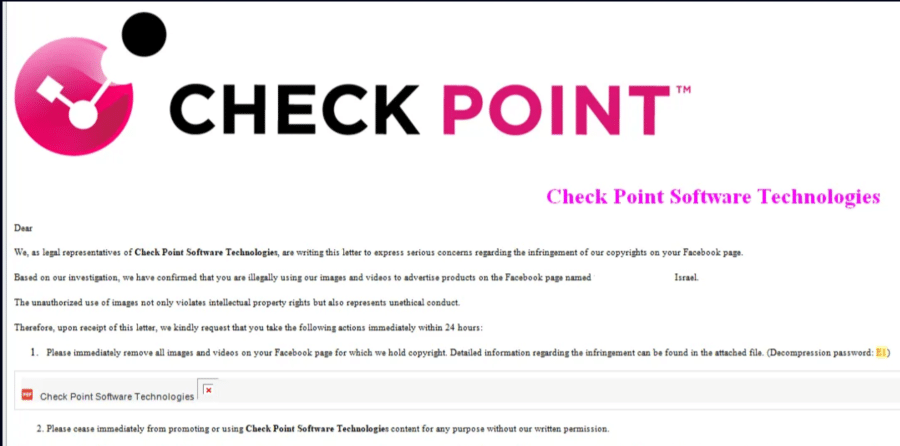
Copyright Infringement Scam
The emails call upon the recipient to download an archive file that triggers the infection through DLL side-loading. “The vulnerable binary then installs the latest version of the Rhadamanthys stealer (version 0.7), which includes new capabilities such as an alleged AI-powered OCR (optical character recognition) module,” says Checkpoint in its report. Essentially, it downloads dangerous malware on your computer if you download the email attachment.
While such attacks are not new and have been reported multiple times in the past where threat actors impersonate leading law firms, what makes this phishing scam problematic is its scale which is spread across continents. Scammers are getting better at tricking people too, using AI and other tools to generate millions of convincing scam emails.
“This discovery of the CopyRh(ight)adamantys campaign reveals not only the evolving sophistication of cyber threats but also highlights how cybercriminals are leveraging AI for marketing purposes and use automation to enhance their reach and operational scale,” said Sergey Shykevich, threat intelligence group manager at Check Point Software.
He added, “For security leaders, it’s a wake-up call to prioritize automation and AI in defense strategies to counteract these globally scaled, financially motivated phishing campaigns.”
Who Is Behind the Attack?
According to Check Point, the campaign is not being run by a particular country but by a group of cybercriminals. “Unlike nation-state actors, who typically target high-value assets such as government agencies or critical infrastructure, this campaign displays no such selectivity. Instead, it targets a diverse range of organizations with no clear strategic connections, reinforcing the conclusion that financial motives drive the attackers,” says Check Point in its report.
🚨 Ongoing, large-scale phishing campaign :
🚩 Copyright infringement lures impersonating dozens of companies spreading Rhadamanthys
🎭 70% of lure firms are in Entertainment/Media & Tech/Software
🤖 "AI-powered" feature is classic OCR techRead more–>https://t.co/UjksxJwzzZ
— Check Point Research (@_CPResearch_) November 7, 2024
How to Protect Yourself From Copyright Scam Phishing Attack
Over the long term, companies likely need to invest more in AI capabilities to counter these attacks. The chance of human error, especially for a large company with many employees, is simply too great to allow these emails to get to employee inboxes. A single downloaded file could devastate an entire corporation.
While keeping these scams out of workers’ inboxes is essential, employees also need a strong understanding of the basic online hygiene so that they are prepared for any kind of phishing scam they run into.
Firstly, one should not panic if they receive an email alleging that their organization indulged in a copyright violation. Fear and greed are two of the emotions that scammers exploit the most and try to create a false sense of urgency to trap gullible recipients. Be extremely careful anytime you are rushed to click on a link or download a file.
Also, if you get such an email, it is always advisable to check if it is coming from a bona fide source. Scammers often make fictitious email IDs on Gmail to make it look like genuine company mail. Make sure that the email is from the correct address before even opening it. If in doubt, reach out to your IT department for help. A few minutes or hours of delay is always far superior to running the risk of a breach.
Finally, when you have any kind of doubt about an email or message, do not open any attachments or links, no matter if they look legit or not, as these are the easiest ways for bad actors to install malware on the device.
Online Scams Are on the Rise
This copyright scam is far from the only recent innovation in the phishing world. Here are some of the key scams to watch out for:
- Investment scams: Investment scams, especially those related to cryptocurrencies are quite popular among cybercriminals. Crypto as an asset class is seeing increased interest and even Donald Trump who has been elected as the 47th US president has also backed digital assets. However, crypto scams are also a sad reality. To save yourself from scams related to investments, just follow one simple rule: “If it’s too good to be true, it probably is”, and avoid schemes that promise abnormally high returns.
- Online shopping scam: Many fake ecommerce platforms have popped up, some selling goods at “too good to be true” prices. Along with the prices, beware of suspicious attempts to get your payment information.
- Sextortion scams: In these scams, scammers manipulate you to send explicit images which are then used for extortion. Sometimes they claim they already have images for blackmail (but they are often lying to cause panic and urgency).
- Fake tech support: Fake tech support is one of the oldest scams in the book where bad actors trick you into believing they are genuine tech support executives of leading companies and then scam you into transferring money to them. While the concept isn’t new, scammers are always coming up with ways to improve their scams.
The list is by no means exhaustive and new scams keep popping up all the time. For instance, social engineering scams are on the rise where scammers exploit your trust and trick you into revealing sensitive information that they can use for fraud. AI voice scams are another menace where cybercriminals can clone the voices of your near and dear ones to scam you.
